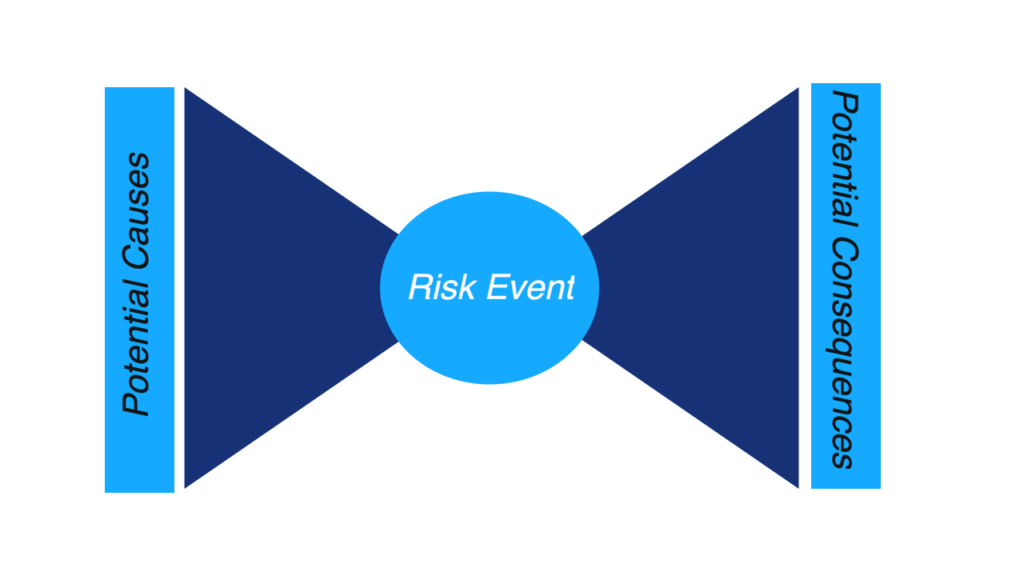
Integrated Risk Management (IRM) is a powerful way to help clients visualize and manage risks by identifying their causes, consequences, and controls in a structured format.
Since our initial post about Bowtie Method, there has been tons of questions surrounding the steps on how to Implement the Bowtie Method in ServiceNow.
The steps below provide high-level, what applications and details to create to begin implementing in ServiceNow.
In this post, we will discuss First 3 Steps to begin within ServiceNow:
1. Define and Scope the Bowtie Risk Framework
- Clarify the purpose of using the Bowtie Method and identify the key risk scenarios the customer wants to model. For example, this might include operational, compliance, or IT risks.
- Confirm whether the customer has already set up Risk, Policy and Compliance applications or if additional configuration is required.
- Ensure to include any subject matter experts who can contribute to defining risk events, threats, controls, and impacts such as risk owners, risk managers.
2. Configure Bowtie Components in ServiceNow
The Bowtie Method consists of core elements: risk events, threats (causes), consequences, and preventive and reactive controls.
Map these in ServiceNow:
- Risk Event: Use the Risk Statement record to represent the central risk event in the Bowtie.
- Create a new risk type or category specifically for bowtie-related risks for clear identification.
- Threats and Consequences:
- Threats (Causes): Map threats as associated causes by creating records in the Risk framework.
- Use fields to identify them as contributing factors or causes.
- Consequences: Map potential consequences as related fields or risk sub-categories tied to the main risk event, so users can see the end results if the risk occurs.
- Controls:
- Preventive Controls: Configure these in Controls framework to show which controls mitigate the risk from materializing.
- Reactive Controls: Also known as “mitigating” or “recovery” controls, configure these controls to show how they reduce the impact if the risk does occur.
3. Set Up Relationships Between Elements
- Establish relationships between risk events, threats, and controls to create a holistic view.
- This is critical for the Bowtie Method, as it visually connects all elements.
- Use ServiceNow’s related lists like m2m table in Risk and Control records to show connections.
- You can also leverage the power of ServiceNow by automating relationships between threats and their respective controls.
Stay tuned for steps 4,5, and 6 …